Authentication & Access Systems

Shift your Web Security to the Cloud, for the Cloud
As enterprises embrace digital transformation, the adoption of software-as-a-service (SaaS) is robust...

Modern upgrade opportunities powered by Veeam DataLabs
With the upcoming end of life of Microsoft Windows server 2008 R2, organizations need to have a plan...

32 Security Experts on Changing Endpoint Security
For many companies, the modern business environment has become a mobile workplace in which employees...

How to Create a Successful Cybersecurity Plan
Along the edge of subway tracks in the UK is a sign that says, 'Mind the gap,' warning passengers to...

Chart Industries vaporizes ransomware and malware
Malwarebytes enables IT to shift its focus to strategic security project work. The company in this case...

10 Endpoint Security Problems Solved By The Cloud Infrographic
The three challenges you're likely facing – cost and complexity, defenses that can't keep up, and overburdened...
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

The 4 Benefits of VPN Elimination
The corporate perimeter as you know it no longer exists. Virtual private network (VPN) vulnerabilities...

Get a Fast Office 365 User Experience
Recommendations for a smooth migration, fast results. A Microsoft Office 365 migration can be daunting....

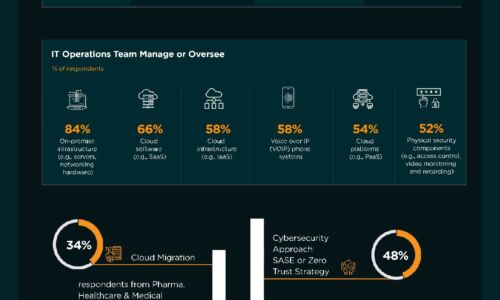
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.