Backhaul

SASE-Ready WAN Edge for the Work from Anywhere Era
Enterprise networks are on the verge of a major tipping point, driven by the shift from employees working...

Core connectivity: The key enabler of digital transformation
The phrase 'digital transformation' is a hot topic across industry right now. Based on the consultancy...

SASE: Beyond the Hype
Solve network and security management challenges with a Secure Access Service Edge architecture This...
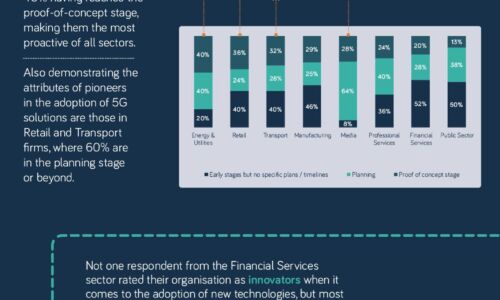
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...
DDoS Attack Threat Landscape — Tracking DDoS Attack Trends in Q2'22
DDoS attacks are on the rise. Ransom attacks reached an all-time high in June 2022, the Ukraine-Russia...

Cloud networks: Shifting into Hyperdrive
Public cloud is driving digital innovation. As IT organizations around the world continue to radically...

5G for the enterprise
With a desire to better understand the current, on-the-ground reality for enterprises and organisations...

Connected cities and places
Improving digital infrastructure is key to enabling a smarter city or place to develop, thereby creating...

Beyond on-demand for DDoS defense
The global pandemic changed the way we work, travel, play, and stay connected — increasing our reliance...

Multi-cloud Load Balancing for Dummies
Legacy hardware-based load balancers don't meet modern enterprise application delivery requirements in...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



