BYOD

VP AppDev Confessions
Development teams burdened with complex release requirements often run over schedule and over budget....

Powering Digital Transformation with a Hybrid Cloud Strategy
It's not news that companies in every industry are fundamentally transforming the way they do business. Scrappy...

BIOS Security – The Next Frontier for Endpoint Protection
Everyone is familiar with the process of booting up a computer. Many of us do this every day — pressing...

CompTIA A+ Certification All-in-One For Dummies, 5th Edition
Fully updated to cover the 2019 exam release! CompTIA's A+ certification is an essential certification...

Fleet ELD mandate
With the ELD mandate in effect, companies with vehicles requiring fleets that use paper logs to track...
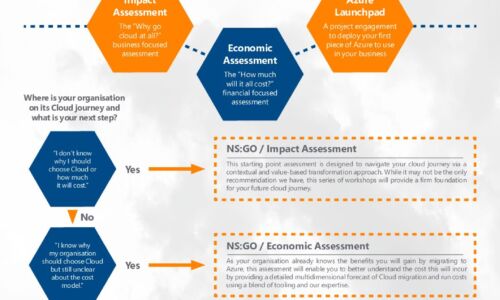
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

The Cloud for Better Comms
Technology has helped businesses make some giant leaps forward. But if you can't keep up with it, the...

Why digital transformation is the only option for businesses today
Over the last ten years, digital transformation has changed the landscape of global business. In this...

Get Total Endpoint Security with KACE
As an IT professional, you're likely under pressure to manage an increasingly complex environment, while...

Time to say yes to NoSQL
This whitepaper from Stratecast and Frost and Sullivan provides expert advice to business technology...

The C-Suite Guide to Digital Business Transformation
Innovative ways to streamline operations Financial businesses face an ongoing challenge – to better...

Evolving From Operating IT To Orchestrating IT
Organisations realise the time is now to move to a new deployment model. Digital transformation and proliferation...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

