BYOD

Building the digital workplace
The days when having a job meant traffic jams, cubicles, and a 9-to-5 schedule are coming to an end....

Beneath The Surface Of Digital Transformation
Digital technology has changed market dynamics. Customers expect great experiences, and digital transformation...

The present and the future of higher education IT
Every sector, business and individual has had to adapt over the last 12 months as a result of the global...

Cyber Security for Dummies
Protect your business and family against cyber attacks Cybersecurity is the protection against the unauthorized...

Mobilising employee productivity in the distributed workplace
Citrix and Microsoft shape modern workplaces that unite the essential elements of today's distributed...
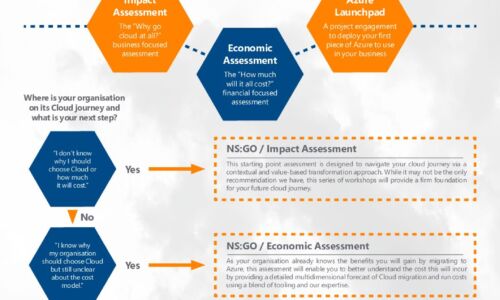
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

5 Steps to Battle Endpoint Cybercrime with KACE
Cyberattacks are increasing across all industries, and cybercriminals are savvier than ever. While the...

Insider Threat Prevention Guide
In a perfect world, trust would never be violated. Cyber defenses would be impregnable. No employee would...

5-minute Primer: MultiLine at Work
What do you do when your employees conduct company business on their personal devices? On one hand, it...

User Risk Report 2018
Risky end-user behaviours are impacting organisations around the world, with implications that can be...

Addressing Security Challenges in Hybrid Cloud Environments
Enterprises are increasingly using hybrid environments, but this move can come with risks and challenges...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


