Cloud Computing

Extracting the Full Value of the Cloud
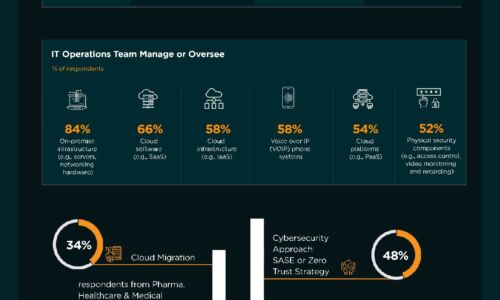
As more enterprises move their IT infrastructures to the cloud and get their software via cloud subscriptions,...

10 Ways to Fortify Ransomware Recovery Defenses
Ransomware has become a 'cyber-pandemic' that shows no signs of diminishing anytime soon. Your ransomware...

Verizon and Palo Alto Networks Enabling a Secure Connected World
Supporting mobility, minimizing the attack surface, and having reliable access to applications are key...

Mind-blowing customer experience starts here
Now is the time to take your digital transformation in a new, more effective direction. At ServiceNow,...

Box and ECM: Key integrations that drive digital transformation
Legacy ECM solutions simply can't keep up with the way you work today. Work is more mobile, more collaborative,...

What you need to know about upcoming ESG regulations
New ESG regulations are being proposed across the world. But ESG is about more than just meeting requirements....

A Unified Workspace delivers a transformative employee experience
A critical business edge comes from employees who are engaged, inspired and happy–thanks to the right...

The CISO’s Guide to Effective Zero-trust Access
Best practices in network access stipulate a zero-trust access (ZTA) approach. CISOs looking to implement...

The Digital Business: What Do Your Customers Expect?
With every week that passes, our dependency on paper wanes as digital processes are introduced into every...

5 Signs MDR Is Right for Your Organization
Perhaps you've been considering a managed detection and response (MDR) solution, but you aren't quite...

Case Study - Amiri Hospital
As a leading healthcare institution in Kuwait, the 415-bed Amiri Hospital viewed its impending expansion...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.