Data Loss Prevention (DLP)

Privileged Access and the Impact of Pass the Hash Attacks
The goal of this survey was to capture hard data on current experiences, trends and approaches to Identity...

20 Examples of Smart Cloud Security
Smart cloud security provides critical capabilities such as governing access and activities in sanctioned...

Case Study - Malwarebytes Endpoint Protection and Response
Malwarebytes cut potential downtime to a matter of hours rather than weeks. Malwarebytes complements...

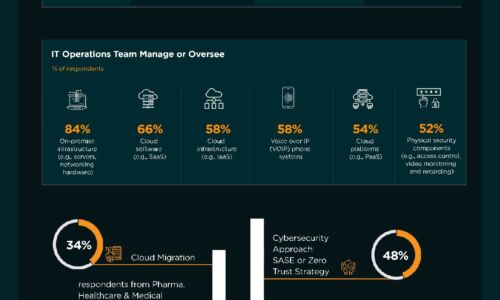
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

The Definitive Guide to SharePoint Migration Planning
Getting your SharePoint migration right is essential to a host of important goals, from business continuity...

The Case for Secure Communications
The tapping of voice communications has occurred virtually as long as electronic communication has been...

Cloud Data Security 2023 Report by ESG, a division of TechTarget
…More than half (59%) of respondents believe that more than 30% of their organization's sensitive data...

Ponemon Cost of Insider Threats Report 2022
External attackers aren't the only threats modern organisations need to consider in their cybersecurity...

Filling the Gaps in Office 365
Office 365 offers a variety of choices and added functionality making it confusing for IT teams to decide...

How Proofpoint Defends Against Ransomware
Stop ransomware from taking root and spreading in your organisation. Ransomware attacks are becoming...

The Hidden Cost of Free M365 Security Features
All email, cloud, and compliance solutions are not created equal. As organisations make the move to Microsoft...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.