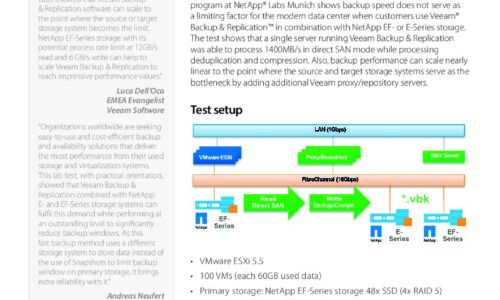
Fibre Channel

Winning in the New Era of Data Management
In the data-driven age, information is as valuable as currency. Entire industries are being disrupted...

CISSP For Dummies
Secure your CISSP certification! If you're a security professional seeking your CISSP certification,...

Security Control Guide: Hardened Services Guide
System Hardening is the process of securing a system's configuration and settings to reduce IT vulnerability...

Windows Server 2019 and PowerShell All-in-One For Dummies
Windows Server 2019 and PowerShell All-in-One For Dummies offers a single reference to help you build...

Cyber Security for Dummies
Protect your business and family against cyber attacks Cybersecurity is the protection against the unauthorized...

Transform Your Field Service with a Great Customer Experience
Full Offline Working, Flexible Architecture, Reusable Components Faced with pressures from both the business...

How media companies thrive in the digital age
As technology and media continue to evolve at a rapid pace, publishers, producers, editors, and filmmakers...

All-Flash Buyer's Guide: Tips for Evaluating Solid-State Arrays
Think Flash-First for Primary Storage. The introduction of enterprise-grade all-flash arrays has turned...

Dell EMC PowerStore: Oracle Database Best Practices
This paper delivers guidance for using Dell EMCTM PowerStoreTM T model arrays in an Oracle® 12cR2 (and...

Ransomware Protection with Veritas NetBackup Appliances
Download this whitepaper to discover how to protect your backup and recovery infrastructure from attacks....

How Cloud Desktops Support Workforce Agility
How fast is the number of devices users employ growing? It has been more than four years since GSMA Intelligence...
- 1
- 2
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.