Hardware
Finding a Setting Worthy of Your “Crown Jewels”
Keep all the Data in a single, unified Database – Oracle Exadata For most companies, data is critical...

Cybersecurity for retail: Prevention is better than the cure
Prevention is almost always better than the cure. But how many organisations are living up to the promise...

6 Steps to Implementing a Zero Trust Model
An all or nothing approach to Zero Trust is a tall task. What if you took a more incremental, agile approach...

Ponemon Report
Ponemon surveyed 1,826 IT professionals globally to understand the state of SD-WAN, SASE and Zero Trust...

Digital Transformation Today
More and more buyers are looking for a digital experience that not only improves challenges like wait-time...

Case Study – Asda
Asda is a UK supermarket retailer, based in Leeds. The business serves more than 18 million customers...
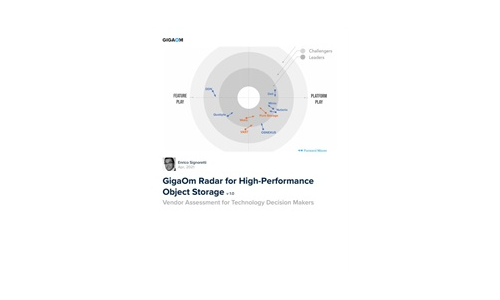
GigaOm Radar for High-Performance Object Storage
For quite some time, users have been asking for object storage solutions with better performance characteristics....

How Cloudflare Bot Management Works
Cloudflare Bot Management applies automated, data-driven approaches to managing bots. By applying machine...

Migrating SAP to the Cloud
Transform SAP into the foundation of your competitive differentiation Enterprises such as BP, Bristol-Myers...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.