Network Infrastructure

Alphabet Soup: Making Sense of XDR, EDR, NDR, and SIEM
XDR, EDR, NDR, and SIEM. They are among the most prominent acronyms in cybersecurity. But what do they...

Nasuni for Rapid Ransomware Recovery
The FBI's Cyber Crime division defines ransomware as 'an insidious type of malware that encrypts, or...

Microsoft Digital Defense Report
Over the past year the world has borne witness to a burgeoning cybercrime economy and the rapid rise...

Protecting Your Hybrid and Hyperscale Data Centers
Organizations are building hybrid data centers that consist of composable and scalable architectures....

How SASE empowers your business for the cloud generation.
Wide area networks (WANs) have played a critical role in business growth for several decades. Early WANs...

Aruba Unified Infrastructure
Network infrastructure and operations teams have never been more stretched. Hyper-distributed edge environments...
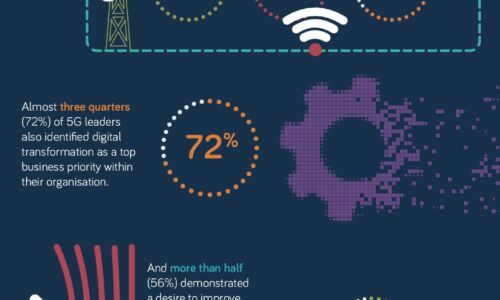
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

The Business Value of VMware NSX Advanced Load Balancer
With NSX Advanced Load Balancer, teams don't have to choose between overprovisioning and potentially...

Insider’s Guide To Choosing a DNS Service
The need that DNS (the domain name system) was created to address seems simple enough: where can I find...

5G Is Changing the Game - Right Now. Is Your Infrastructure Ready?
Advanced 5G use cases will require a fundamental change in infrastructure before they can scale. As network...

Five Best Practices for Mitigating DDoS Attacks
Distributed denial-of-service (DDoS) attacks remain one of the most effective methods used by cybercriminals...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


