Network

Ponemon Cost of Insider Threats Global Report
Independently conducted by Ponemon Institute External attackers aren't the only threats modern organisations...

Introduction to AWS Security
Raise your security posture with AWS infrastructure and services. AWS's approach to security, including...

Delivering Real-time Cloud Security Without Trading Off Performance
There has been a long-standing tradeoff between security and performance, and security often gets the...

10 Benefits of Oracle's Data Management Platform
Accelerating business change begins with the proper management of an organization's data. With Oracle's...

Enduring from Home: COVID-19's Impact on Business Security
Faced with shelter-in-place orders in their home counties and states, countless companies transitioned...

Cloud-delivered security for the digital workspace
With the adoption of hybrid cloud and the rise in remote work, traditional connectivity models like VPN...
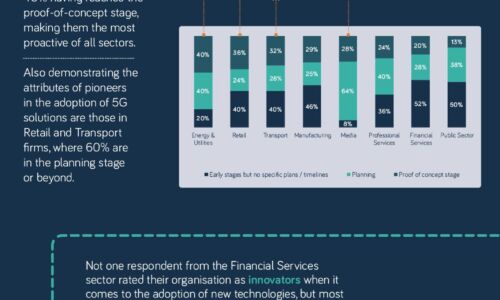
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

IPv6 migration with Micetro by MenandMice
IPv6 adoption has been slow in the corporate world. Despite global IPv6 traffic increasing with 500%...

5 Critical Requirements for Internal Firewalling in the Data Center
Preventing hackers from hiding inside large volumes of east-west network traffic has now become critical...

10 Biggest and boldest insider threats
Over the last two years alone, insider security incidents have jumped 47%, with the average cost per...

A Pure Primer AI, Analytics and the Future of your Enterprise
Data is transforming not only businesses, but entire industries, and the world as we know it. As a global...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


