Network

Endpoint security versus productivity in utilities: a false choice?
Utility companies are often targeted because they can be used so effectively as phishing lures, as they...
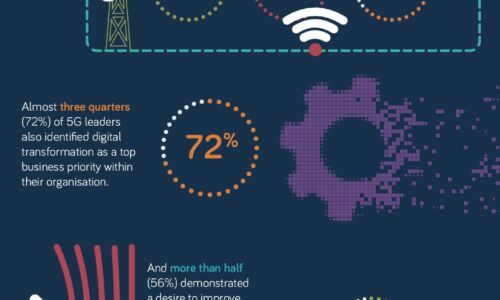
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

NAIKON: Traces from a Military Cyber-Espionage Operation
NAIKON is a threat actor that has been active for more than a decade. The group focuses on high profile...

Best Practices for Database Consolidation
Information Technology (IT) organizations are under pressure to manage costs, increase agility, ensure...

CMO's Guide to AI for Customer-Centric Marketing
AI allows marketing leaders and their teams to quickly analyze vast amounts of customer data to predict...

3 Reasons to Choose Managed Detection and Response
Cyber threats affect data security in all organizations, but organizations in highly regulated industries...

3 Ways to Make Cloud your Business eBook
The role of IT infrastructure and operations leaders has dramatically changed, and cloud evolution continues...

5 steps to successfully deploying a healthy CMDB
Your path to total service visibility and great service availability. Your CMDB is a critical tool for...

QBE Strengthens Zero Trust Posture with Illumio
As one of the world's largest global insurers, QBE's security priorities include the need go faster safely,...

A Buyer's Guide to Optimizing Remote Employees' Extended Network
The shelter-in-place mandates put in place earlier in 2020 sent most employees home, and for the next...

The PC Lifecycle Continuum: From Control to Transformation
As diverse organizations seek to implement data-driven strategies, the personal computer in all its varieties...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


