SAN

How Rapac Energy Saves Weeks of Work by Securing Their OT with Cyolo
A leading power plant operator, Rapac Energy, was looking to securely provide access to their OT and...

2021 Buyer’s Guide to Comprehensive Cloud Security
Cyber resilience comes when you've secured your multi-cloud infrastructure and enabled your DevSecOps...

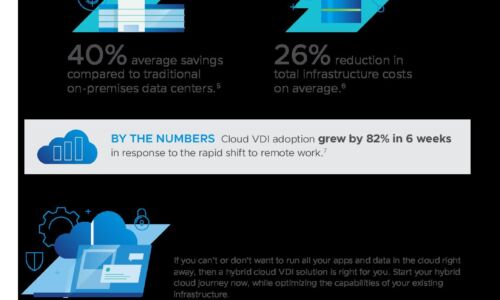
Cloud Operations eBook
No matter where you are on your cloud journey, AWS Cloud Operations can help you speed up innovation...

State of Ransomware: Invest now or pay later
Ransomware attacks continue at a blistering pace because organizations remain vulnerable to the exploits...

The CIO’s guide to aligning technology and business strategy
Hyperautomation and low code edition Inside this CIO Guide, you'll find solutions to the problems that...

The top 3 benefits of predictive intelligence in service operations
The demand for better, faster, cheaper and more scalable IT services and operations has never been greater....

Enterprise NoSQL For Dummies
NoSQL represents a fundamental change in the way people think about storing and accessing data, especially...

Redefining Healthcare in the Cloud
Helping you visualise clinical healthcare innovation, and the future of personalised experiences in the...

Why This Global Bank Trusted BlackBerry to Evaluate its Security Vendor
Staff at this global bank use mobile devices and applications extensively to stay connected and productive....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.