Latest Whitepapers

KuppingerCole Report: Privileged Access Management
Privileged Access Management (PAM) is one of the most important areas of risk management and security...

Managing Critical Events with BlackBerry Alert
Every day, organizations face risks from natural, technological, and human-caused critical events. While...

Hyperconverge Microsoft SQL Server to Simplify Application Delivery
To run SQL workloads efficiently, you need the low cost and high performance of hyperconverged infrastructure...

Fleet ELD mandate
With the ELD mandate in effect, companies with vehicles requiring fleets that use paper logs to track...

Harden Your Defenses With Security Analytics
Analyze data in real time with the right SIEM approach. It's time to step up your security game. If you...
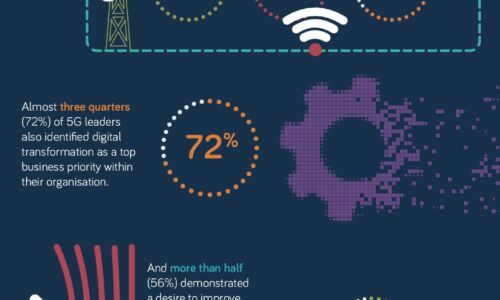
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

The Complete Guide to Enterprise Ransomware Protection
The SentinelOne Complete Ransomware Guide will help you understand, plan for, respond to and protect...

Get the Growth Engine Playbook for Online Trading Platforms
Turbo-charge your growth with smoother experiences and better payment capabilities. Key Findings We know...

The Cybersecurity fail-safe: Converged Endpoint Management (XEM)
Organisations are experiencing more attacks than ever before. Cybersecurity Ventures expects a ransomware...

Checklist: How good is your communications system?
How good is your communications system? Today's work takes place in the office, at home, and everywhere...

How Agencies Use Analytics for Better Decision-Making
Today's agencies need better systems to help them make the most of their data. In this GovLoop report,...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.








