Latest Whitepapers

How to Build a Lightning- Fast, Multi-Petabyte Backup Repository
IT teams are facing exponential data growth. It's natural to worry about exceeding capacity, wondering...

ERP Modernization Is Business Transformation
Learn how a cloud-based ERP system can help your organization get better business insights, increase...

Transform Your Field Service with a Great Customer Experience
Full Offline Working, Flexible Architecture, Reusable Components Faced with pressures from both the business...
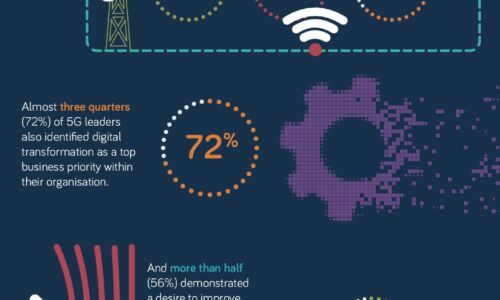
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

How to Ensure your Digital Experience Platform is Right for your Needs
Customers' expectations have never been higher. We all expect more, especially online. We want experiences...

Cloud Data Security 2023 Report by ESG, a division of TechTarget
…More than half (59%) of respondents believe that more than 30% of their organization's sensitive data...

Threat Intelligence Critical to Cyber Security Protection
Financial services institutions are at the forefront of cyber-attacks and keeping information safe is...
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Enterprise NoSQL For Dummies
NoSQL represents a fundamental change in the way people think about storing and accessing data, especially...

The Business Value of Red Hat Enterprise Linux
Linux has firmly established itself as a preferred delivery vehicle for modern applications, in addition...

Protecting your content against cyber threats and data loss
How the Content Cloud safeguards your most valuable information Your business runs on content — but...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.








