Authentication & Access Systems

Use Case-Driven Cloud Security Evaluator Guide
Researching cloud security? Be sure you evaluate yourself and your vendors on the 6 most common cloud...

How to Create a Successful Cybersecurity Plan
Along the edge of subway tracks in the UK is a sign that says, 'Mind the gap,' warning passengers to...

Cloud Security: From Start Point to End Point
Cloud computing offers organisations competitive advantages such as increased speed, agility, scale and...

How Malware Can Steal Your Data
As applications drive business, more and more valuable data is accessed and exchanged through them. Cybercriminals...

Cybersecurity Insiders: Cloud Security Report
The 2019 Cloud Security Report from Cybersecurity Insiders highlights what is and what is not working...

Why you need an adaptive security segmentation solution
The threat landscape is more dynamic than ever before, and as business-critical applications traverse...

The 4 Benefits of VPN Elimination
The corporate perimeter as you know it no longer exists. Virtual private network (VPN) vulnerabilities...

Chart Industries vaporizes ransomware and malware
Malwarebytes enables IT to shift its focus to strategic security project work. The company in this case...
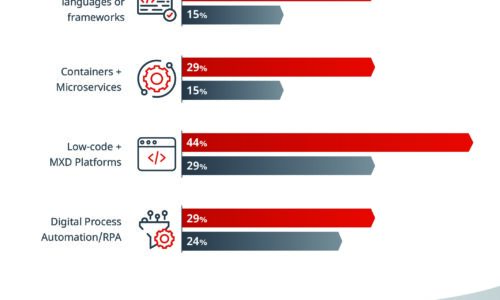
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...

Securing Cloud Transformation with a Zero Trust Approach
When it comes to rates of change, cybersecurity has rightly been on the conservative side. Setting up...

10 Endpoint Security Problems and How to Solve Them
Companies are facing massive cybersecurity challenges – many of which are rooted in the endpoint. In...

Get a Fast Office 365 User Experience
Recommendations for a smooth migration, fast results. A Microsoft Office 365 migration can be daunting....

Cyber Security for Dummies
Protect your business and family against cyber attacks Cybersecurity is the protection against the unauthorized...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
