Cloud Computing

2021 State of the Intelligent Information Management Industry
2021 is shaping up as a year of opportunity for many organizations in building out their information...

Speed Up Your Digital Transformation With The Cloud
In this Content Services in the Cloud Guide by AIIM, we explore how companies are tackling critical document...

Software Testing in a Post Pandemic World
Sauce Labs offers the broadest mobile testing solution in the industry to help modern mobile development...

ServiceNow + Vonage: The Perfect Combo
Video Overview of Vonage Contact Center and ServiceNow - Vonage Contact Center (VCC) for ServiceNow integrates...
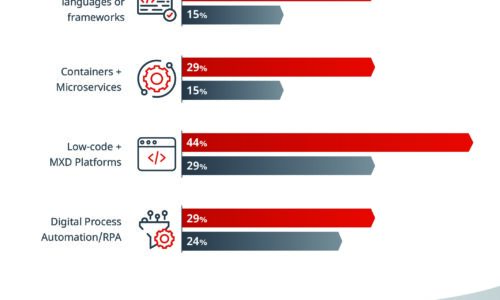
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...

Building a Digital Infrastructure for the Entire Organization
Building a Digital Infrastructure for the Entire Organization Today's business world increasingly demands...

3 steps to accelerating innovation with low-code app development
Digital transformation can put a heavy burden on your app development. You must reduce your backlogs...

The Forrester Wave™: DDoS Mitigation Solutions, Q1 2021
Cloudflare Named A 'Leader' in The Forrester Wave™: DDoS Mitigation Solutions, Q1 2021 Forrester Research,...

Seven reasons why your enterprise needs intelligent search
Organizations are hungry to use data to grow and improve performance, but enterprises are struggling...

Top Segmentation Attributes to Simplify Zero Trust
As the concept of zero trust has gained traction, confusion has increased with regard to what it entails,...

The Benefits of the Cloud: A Guide for IT Leaders
Increase your organization's resiliency and agility. Working with agility and driving innovation can...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


