Compliance

Manage less. Build Faster. Innovate more.
Learn why AWS is the best place to build modern apps Through our experience building applications for...

Best-in-Class SaaS Performance
The average person uses 36 cloud-based services every single day. Now it's up to IT operations teams,...

The Behavox Enterprise Conduct And Risk Report
The Behavox Enterprise Conduct and Risk Report, which surveyed 3,000 corporate professionals and 600...

Business Value of Cloud Modernization
Explore the business value of proven modernization paths Understanding the business value of infrastructure...

GigaOm Radar for Phishing Prevention and Detection
Get your complimentary copy of this independent GigaOm Research report, which analyzes positioning and...
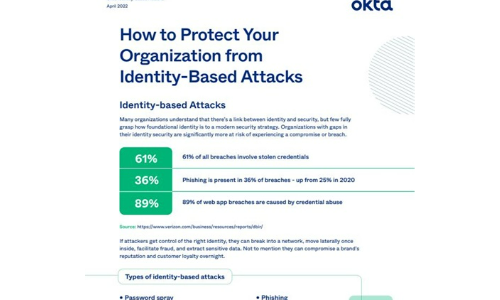
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

10 Biggest and boldest insider threats
Over the last two years alone, insider security incidents have jumped 47%, with the average cost per...

Ransomware Survival Guide
Be Ready for Ransomware Ransomware is an old threat that just won't go away. While overall volumes have...

How to Build Your Microsegmentation Strategy in 5 Steps
A breach to your organization's network is not a question of if, but when. Are you prepared with a micro-segmentation...

Balancing Business Continuity with Innovation
Organisations can still remain innovative during times of crisis. With Workday, you can lead your organisation...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



