Connectivity

UCaaS: Unification and transformation
Enterprise businesses are constantly evolving and transforming. Digitalisation agendas, new strategies...

Making all the right connections
Ask someone how they feel about a company, and they'll have an immediate response. All too often it's...

Secure Access Service Edge Palo Alto Networks SASE Comparative Report
This comparative test was commissioned by Palo Alto Networks to evaluate the security efficacy of leading...

The Definitive Guide To SASE
What is Secure Access Service Edge (SASE) and why do you need it? Download the new guide to learn how...

Next-Gen iPaaS For Dummies
Digital Transformation changes expectations: better service, faster delivery, with less cost. Businesses...
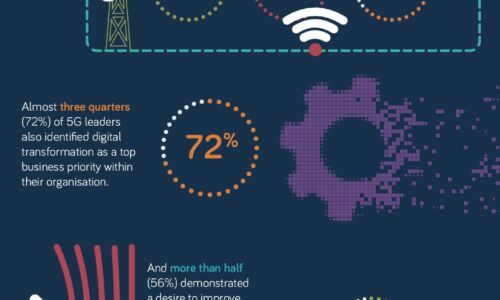
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

Quest Toad for Oracle Tips and Tricks
Toad® for Oracle has been the IT community's tool of choice for more than a decade. With Toad, you are...

Insider Threat Prevention Guide
In a perfect world, trust would never be violated. Cyber defenses would be impregnable. No employee would...

Redefining Modern Enterprise Storage for Mission-critical Workloads
The digital business demands being placed on enterprise-scale IT organizations are now so extreme that...

Moving to a Cloud Data Warehouse on Amazon Redshift
The challenge for today's enterprises is to extract the most value from their data. To do so, companies...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



