Connectivity

Dell PC as a Service
Today's workforce relies on their PCs and accessories to get work done anytime and from anywhere. Users...

Aruba’s Roadmap To Hybrid Workplace Success
After the initial network overhaul to enable work from home at the start of the pandemic, organizations...

One plan, no Excel, real-time decisions with HP Inc.
For years, managers at HP Inc. faced a daunting task when it came time to brief their CEO on the com-pany's...

Proofpoint Information and Cloud Security Platform
The Proofpoint Information and Cloud Security platform combines many of our products to address secure...

Artificial Intelligence: The Smarter Approach To Information Security
The news headlines are replete with stories of devastating data breaches, compromising the personal and...

The Total Economic Impact™ Of VMware Carbon Black Cloud
Security and IT teams today are constantly dealing with overly complex and siloed toolsets that can't...
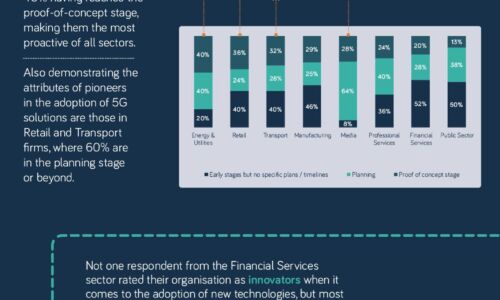
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

Insider Threat Prevention Guide
In a perfect world, trust would never be violated. Cyber defenses would be impregnable. No employee would...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.





