Connectivity
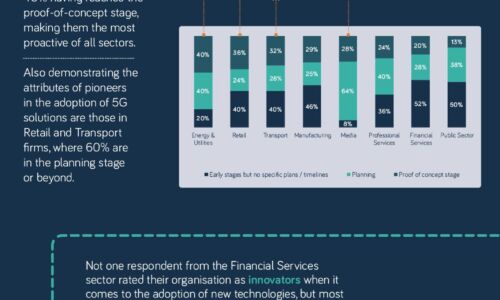
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

Secure Digital Transformation Requires Identity-Based Access Control
Digital transformation is an all-encompassing term that refers to a wide swath of activities designed...

Modernize and Thrive with Device as a Service
Supporting work from anywhere. Addressing evolving security threats. Lowering IT spend. These are the...

Taking Healthcare to the Edge
A global pandemic now extending into its second year has caused disruption, dislocation and distress...

Zero Trust Access for Dummies
As businesses continue to embrace digital innovation, cloud applications, and the new work-from-anywhere...

Healthcare IoT, the RX for Providers and Patients
Healthcare providers have a lot on their plates. Costs are always on the rise, and staff shortages put...

Leadership trends report: customer experience roadmap 2022-2025
Leaders have always needed to innovate to meet demands from the business and customers, but recently...

Unified Communications as a Service
As businesses increasingly embrace a cloud-first strategy, many are migrating their most heavily used...

Public Sector Cloud Journey
As the government continues to move workloads to the cloud, many agencies are struggling to automate...

How to Build a Micro-Segmentation Strategy
Micro-segmentation reduces your attack surface and prevents the spread of breaches inside your data center...

SASE: Beyond the Hype
Solve network and security management challenges with a Secure Access Service Edge architecture This...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


