Connectivity

UCaaS: Unification and transformation
Enterprise businesses are constantly evolving and transforming. Digitalisation agendas, new strategies...

Modernize application delivery with cloud services
The pace of digital transformation is accelerating as businesses adapt to changing customer expectations....

VMware Multi-Cloud Architecture: Enabling Choice and Flexibility
In today's world, application growth is unprecedented and enterprise applications on a wide range of...

EMA Report: Availability and Buying Options in the Emerging SASE Market
Cloudflare One reviewed as a leading provider of Secure Access Service Edge Gartner's Secure Access Service...

Frost Radar™: Global SD-WAN Vendor Market,2021
Aruba earns accolades from Frost and Sullivan. Check out the Frost Radar™: Global SD-WAN Vendor Market...

Unified Communications as a Service
As businesses increasingly embrace a cloud-first strategy, many are migrating their most heavily used...

CRM Evolved Introducing the Era of Intelligent Engagement
Digital Transformation, a key focus of successful organizations, proves itself a business imperative,...

Aruba's Roadmap To Hybrid Workplace Success
After the initial network overhaul to enable work from home at the start of the pandemic, organizations...

The Gorilla Guide to Rapid Restores with Flash and Cloud
Welcome to this Gorilla Guide covering enterprise data protection, backup, and recovery. The purpose...

Defend Yourself Against Ransomware and Other Types of Malware
The May 7, 2021, ransomware attack on U.S. fuel network Colonial Pipeline left millions afraid they couldn't...
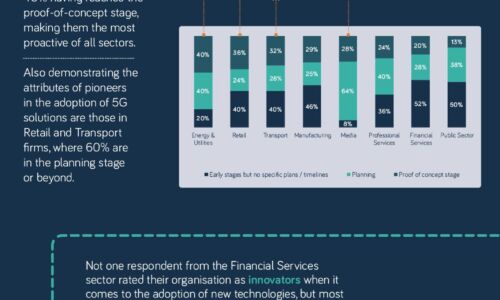
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


