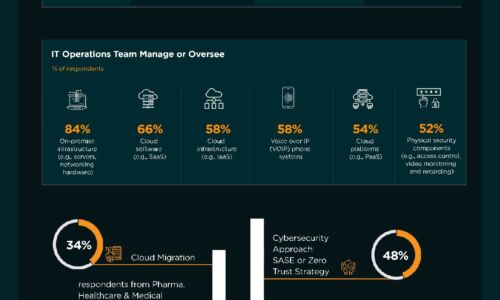
Data Recovery
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Transforming Security in the Mobile Cloud Era
In the age of digital transformation, maintaining secure interactions among users, applications, and...

20 Examples of Smart Cloud Security
Smart cloud security provides critical capabilities such as governing access and activities in sanctioned...

Combatting Ransomware by Exposing the Myths
Ransomware continues to pose a credible and costly threat to the enterprise. Misinformation only compounds...

Decoupling security from the network: The evolution of segmentation
You rely on the network to deliver applications. But as IT scales in size, connectivity, and environments...

Security Starts Here: Privileged Access Management
The threat of a security incident or critical error is very real, and it's something that auditors are...

Why Corelight Is Your Best Next Move In Enterprise Security.
Despite spending billions annually on security infrastructure and services, even the most sophisticated...

The 4 Benefits of VPN Elimination
The corporate perimeter as you know it no longer exists. Virtual private network (VPN) vulnerabilities...

Dell Technologies Continuously Modern Storage eBook
In a modern, data-driven economy, business success—or conversely, business struggles—often equate...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.