
10 Security Tips for Businesses
SECURITY THAT PROTECTS YOUR BUDGET Vanishing budgets, reckless users, infected machines, unpatched software...

Legal Practice in a Hyper-Connected World
Essential Capabilities and Branding for the New Digital Client. Technology is changing the way that businesses...

The Gorilla Guide to Achieving IT Asset Management Success
ITAM is about knowing what you've got, where it is, who's using it and how much it costs. If you want...

Chatbot Starter’s Guide
Is your contact center struggling to determine which chatbot solution is right for you? This eBook can...

The Ultimate Guide to Cyber Hygiene
It's critical for organizations to deeply understand their risk posture and have tools in place that...

PCI Compliance Best Practices
The Payment Card Industry Data Security Standard (PCI DSS) has been in place since 2004, with the latest...

Cyber Security for Dummies
Protect your business and family against cyber attacks Cybersecurity is the protection against the unauthorized...
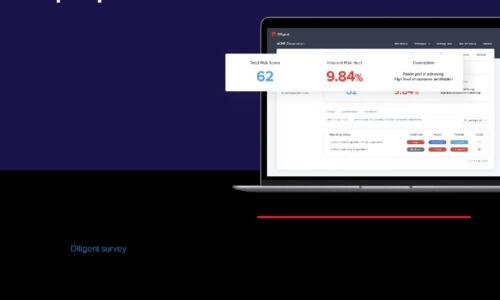
Effective CISO Presentations to the Board: Top Tips & Checklist
As a CISO, you have crucial info to convey about cyber risk, and your board wants to hear it. In a recent...

Modernize Your Legacy Applications in the Cloud
In the last year, enterprises and industries of all kinds faced rapidly changing business environments...

Securing applications in the education industry
The role of technology in education has changed radically in the last two years. Like many other areas...

Reimagine How Work Gets Done - Introducing Fujitsu Work Life Shift
It's time to reimagine a new future. The concept of the workplace has changed forever. It's no longer...

Enterprise NoSQL For Dummies
NoSQL represents a fundamental change in the way people think about storing and accessing data, especially...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

