Mobile Security

LogRhythm for SWIFT Customer Security Controls Framework
Society for Worldwide Interbank Financial Telecommunication (SWIFT) facilitates a huge number of financial...

Delivering Fast and Secure Enterprise Applications
Adopting a zero trust security model — authenticating and authorizing every request, device, and user...

Rackspace Fanatical Support for AWS
As organizations move their workloads from traditional data centers to AWS, IT security paradigms are...

Get a Fast Office 365 User Experience
Recommendations for a smooth migration, fast results. A Microsoft Office 365 migration can be daunting....
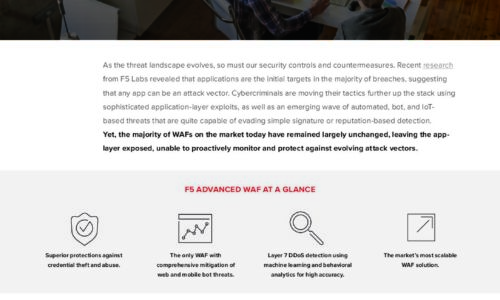
Is Your WAF Keeping Pace with Today’s Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

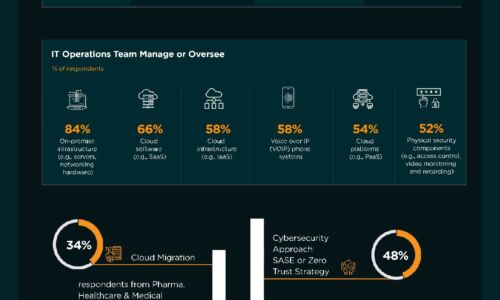
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

How to Create a Successful Cybersecurity Plan
Along the edge of subway tracks in the UK is a sign that says, 'Mind the gap,' warning passengers to...

Decoupling security from the network: The evolution of segmentation
You rely on the network to deliver applications. But as IT scales in size, connectivity, and environments...

Fleet Management and Compliance Mini Guide
When you increase compliance and reap great rewards in return, that's a win-win. Especially when the...

Cloud Security Generation Z
Also known as the 'Cloud Generation,' this Generation Z is already reshaping IT…and careers. Many are...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.